
Learn about common Bluetooth attacks like Bluesnarfing, MITM, and Bluebugging. Discover real-life scenarios and tips to secure your devices against Bluetooth threats.... Read More

Learn about common Bluetooth attacks like Bluesnarfing, MITM, and Bluebugging. Discover real-life scenarios and tips to secure your devices against Bluetooth threats.... Read More
Explore the simplicity and elegance of GNOME desktop environment with our curated gallery of 25 stunning images showcasing its design and functionality.... Read More

Discover the beauty of KDE Plasma Desktop with our curated gallery of 30 stunning images showcasing its elegance, customization, and modern design.... Read More
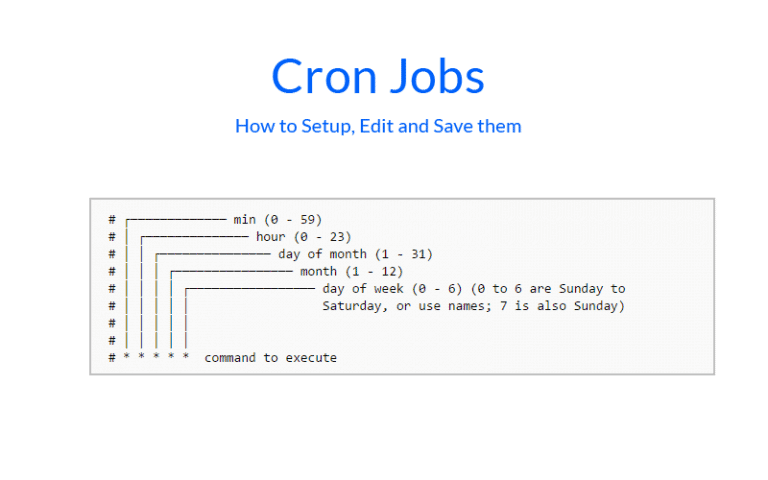
Learn about cron jobs and how to use them effectively in this beginner's guide. Understand cron job syntax, scheduling options, and examples for automating tasks on Unix-like operating systems.... Read More

Discover how Germany is leading the charge in embracing open-source software, transitioning away from proprietary solutions towards digital sovereignty. Learn about the state of Schleswig-Holstein's commitment and the implications for global tech trends... Read More