
Discover how WhatsApp can be hacked, with detailed insights into various attack types and scenarios. Learn how to protect your account from potential threats.... Read More

Discover how WhatsApp can be hacked, with detailed insights into various attack types and scenarios. Learn how to protect your account from potential threats.... Read More

Learn about common Bluetooth attacks like Bluesnarfing, MITM, and Bluebugging. Discover real-life scenarios and tips to secure your devices against Bluetooth threats.... Read More
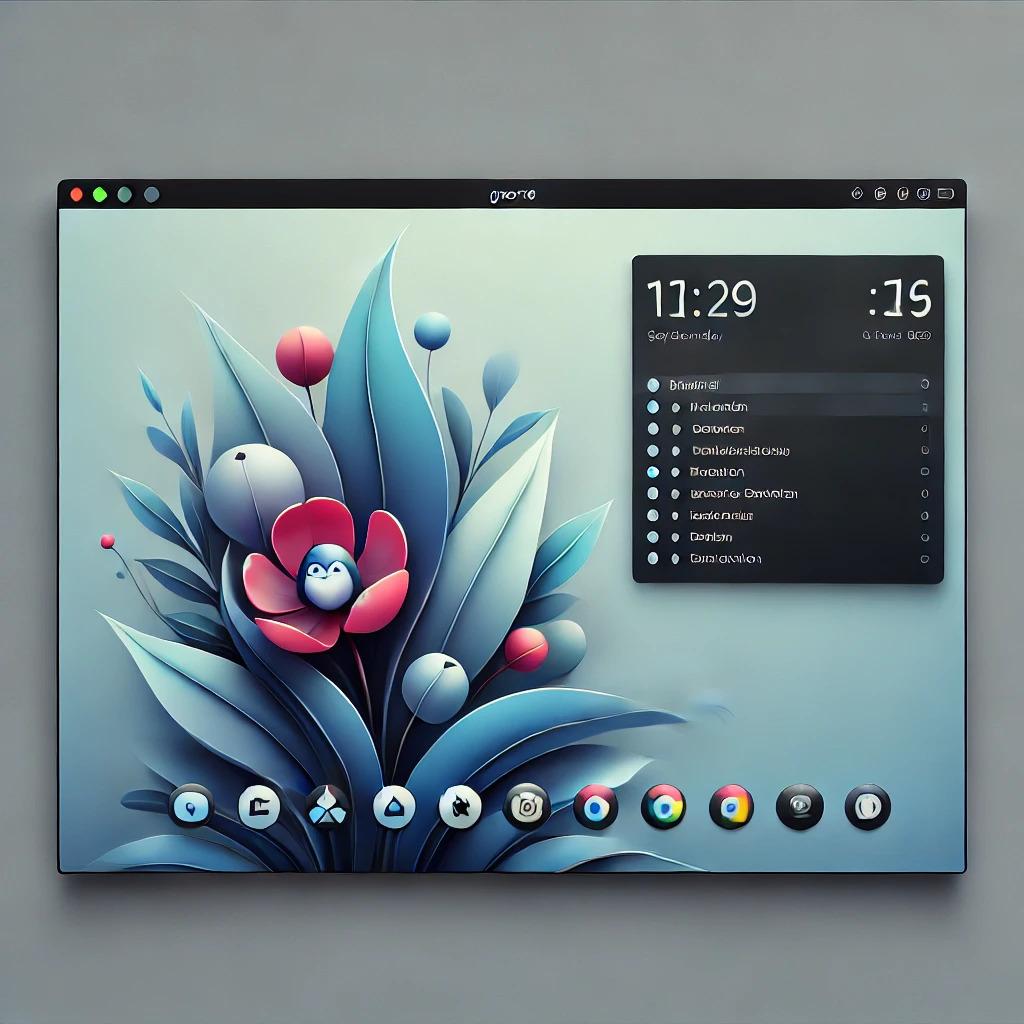
Explore the simplicity and elegance of GNOME desktop environment with our curated gallery of 25 stunning images showcasing its design and functionality.... Read More

Discover the beauty of KDE Plasma Desktop with our curated gallery of 30 stunning images showcasing its elegance, customization, and modern design.... Read More

Doctor Who, the longest-running sci-fi TV show since 1963, continues to captivate millions worldwide with its innovative storytelling, unforgettable characters, and enduring appeal.... Read More