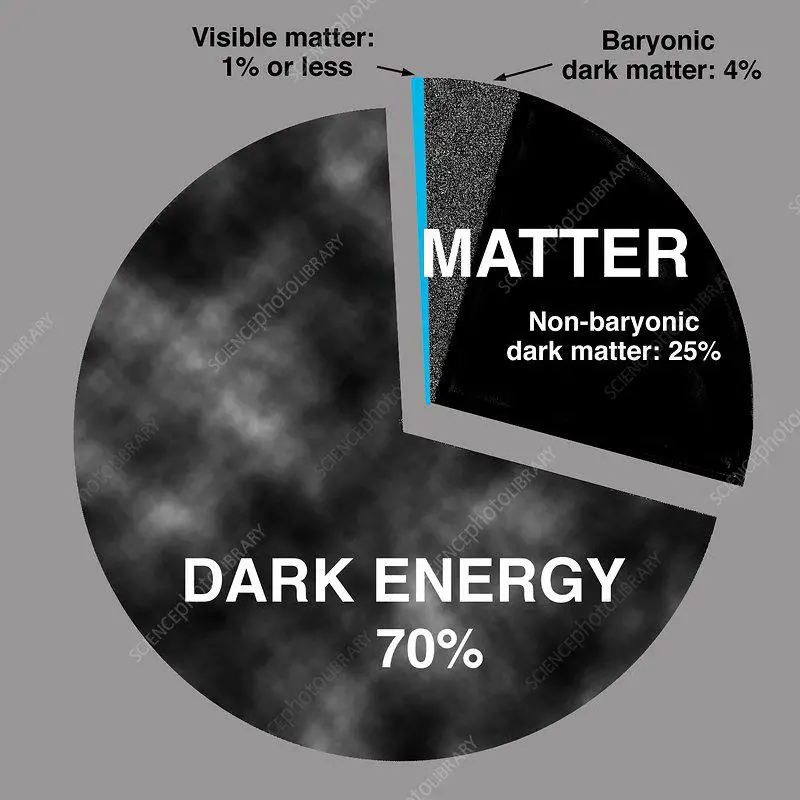
L'ère du vide" (The Age of the Empty) is a thought-provoking book by the French philosopher and sociologist Gilles Lipovetsky. Published in 1983, the book analyzes the cultural and social changes that took place in the late 20th century and predicts the direction in which our society is heading... Read More